| Windows Startup Programs database | RegRun Trojan Analyser |
|
On-line Guide Help On-line Screenshots Localization NI Forum Mickey Forum Greatis Forum Startup Programs Application Database Hot! Download: RegRun 4.0 beta 2 What's new?
|
Trojan Analyser allows to determine if a suspicious file is useful or harmful.
Trojan Analyser traces all files that the application tried to open or write, and all registry operations.

Trojan Analyser has two methods to begin tracing:
Note!
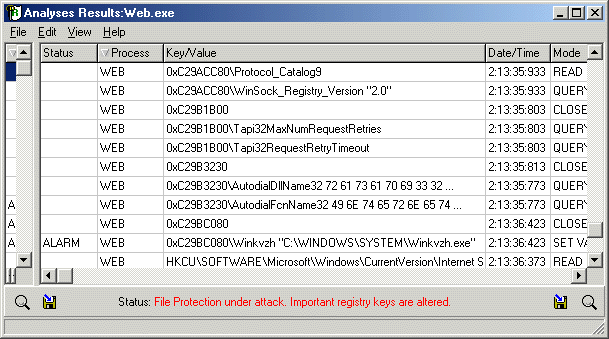
After finishing tracing Write-Protection mode will be automatically cancelled. 2) Trojan Analyser automatically checks your execution file extensions (exe, com, pif, bat) before starting tracing and after finishing. If the file extensions will be changed they will be restored by Trojan Analyser. This will protect you against viruses actions. We suggest you to check your system by WatchDog or run Start Control to restore changes in the startup. After the application finished, or you stop its work, you will see the results in the Results window. You may quickly inspect changes by using search and sort operations. Also, you may export results to CSV file format. You may use Excel or another application to analyse them. Look at the sample results of the Klez virus actions:

Trojan Analyser doesn't allow to create virus file.
RegRun Start control will warn you about changes in the registry startup keys and allow to decline these changes.
Try RegRun now!Read more information >> |